Modern organizations and/or businesses are increasingly adopting a “cloud first” approach to their IT infrastructure, which means they rely on public clouds for many of their computing needs. This shift has created new challenges for enterprises as it comes with increased risks associated with data loss or theft due to the lack of control over physical assets and access to sensitive information stored within them. In addition, there have been several high-profile breaches involving stolen credentials from third-party vendors who provide services such as email hosting, web application firewall protection, etc., where attackers were able to compromise these accounts and gain unauthorized access to customer systems. These attacks highlight how critical it is for companies to ensure that all aspects of their business operations remain secure when using public clouds.
What is cloud security posture management?
The term “security postures” refers to an organization’s overall state of readiness regarding its ability to protect itself against cyber threats. The goal of Cloud Security Posture Management is to help organizations identify areas where they may be vulnerable to attack by leveraging advanced threat intelligence techniques and automated tools to proactively detect potential vulnerabilities before any malicious activity can occur. By doing so, you will be better prepared to respond quickly should your network become compromised.
How CSPM works?
Cloud Security Posture Management leverages machine learning algorithms to analyze hundreds of thousands of events per day across multiple sources, including logs generated by various applications running on virtual machines, log files collected from servers and endpoints, and alerts received from SIEMs and IDP providers. It then uses this rich dataset to build models that predict future behavior based on past observations. Once trained, these models continuously monitor each system at runtime and alert administrators if suspicious activities are detected. Administrators receive real-time notifications via Slack, SMS, Email, Push Notifications, Webhooks, API calls, Syslog messages, etc., depending upon the type of event being monitored.
Why use CSPM?
There are three main reasons why organizations choose to implement CSPM: visibility, governance, compliance.
• Visibility
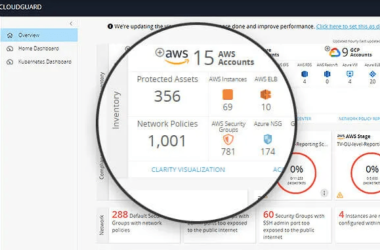
By implementing CSPM, you get visibility into what is happening across your entire environment at every level – including individual applications, servers, networks, users, devices, and more. You also receive alerts whenever something changes, allowing you to take action immediately if necessary. With this type of visibility, you can easily spot anomalies and determine whether anything suspicious is occurring. For example, if one user suddenly starts accessing files outside their normal work area, then you know that someone might be trying to steal company secrets. Or perhaps some malware was recently installed onto a server without anyone noticing. If you find out about either situation early enough, you can stop it before it becomes too late.
• Governance
When implemented correctly, CSPM provides a framework for managing your organization’s cybersecurity posture. It helps you understand exactly what each part of your system does and gives you insight into how well those parts are performing. When appropriately used, CSPM allows you to make informed decisions based on real-time metrics rather than relying solely on historical reports. As a result, you’ll be able to see trends and patterns that could indicate future problems. With CSPM, you’re not just looking at the status quo; instead, you’re actively monitoring everything going on inside your environment. That way, you can catch issues before they happen and prevent damage from spreading throughout your network. And because CSPM uses machine learning technology, it learns from past events and makes predictions about what will likely happen next. So even though it doesn’t always give 100% accurate results, it still offers valuable insights that allow you to act faster and more effectively.
As mentioned earlier, CSPM enables you to monitor your entire environment, but it goes beyond simply tracking down intrusions. Instead, it lets you manage your cybersecurity posture through proactive measures like patching, updating software, configuring firewalls, securing privileged accounts, and ensuring appropriate password policies. This means that when you do discover a problem, you have already taken steps to fix it. In addition, CSPM monitors all aspects of your infrastructure, including physical assets and virtual ones. Because it covers such a wide range of systems, it ensures that you won’t miss anything important no matter what happens within your IT department.
• Compliance

Finally, CSPM helps ensure that your organization complies with industry standards and regulations. By using CSPM, you can quickly identify any potential risks and address them accordingly. The best thing about CSPM is that it works seamlessly alongside existing processes, so there aren’t additional costs associated with adding new tools. Plus, since it integrates directly with Microsoft Azure Active Directory, you don’t need an extra toolset to use it.
CSPM best practices
Here are some tips to help you implement CSPM successfully:
* Use the suitable data sources
Make sure that you only collect information relevant to your business needs. Don’t include personal details unless absolutely required by law. Also, avoid collecting sensitive information like credit card numbers, social security numbers, passwords, etc., because these types of records may contain personally identifiable information.
* Keep track of compliance requirements.
You should keep track of all applicable laws and regulations related to your company. For example, if you operate under HIPAA or PCI DSS rules, then you must comply with their guidelines.
* Implement governance procedures.
Governance refers to the process of establishing clear expectations around who has access to what resources and why. You should also establish roles and responsibilities for different groups within your organization. These might include employees, contractors, partners, vendors, customers, suppliers, and others.
* Identify critical assets.
It’s essential to know where your most vital assets reside. If you want to protect them, you need to determine whether they exist outside your firewall. If they do, then you need to consider implementing appropriate controls. Otherwise, you shouldn’t worry too much about protecting them.
* Prioritize threats.
Once you’ve identified your key assets, you need to decide which vulnerabilities pose the greatest threat. Then you need to take action against those threats. To accomplish this, you first need to assess the severity level of each vulnerability. Next, you need to rank them based on how likely they are to be exploited. Finally, you need to assign priorities to each one.
* Monitor changes.
Once you’re done prioritizing threats, you need to make sure that nothing gets overlooked. That way, you can react immediately whenever something does go wrong. It’s beneficial to regularly scan logs for suspicious activity. However, you should always perform regular scans regardless of whether you find anything unusual. This will allow you to catch problems before they become a problem.
* Maintain visibility into your environment.
To monitor your network effectively, you need to have complete visibility across every aspect of your infrastructure. In addition to monitoring traffic flows, you should also check system health indicators such as CPU utilization, memory usage, disk space, and more. Furthermore, you should periodically run performance tests to verify that everything is working properly.
* Ensure proper documentation.
If you don’t document your processes well enough, it could lead to severe issues down the road. Therefore, you should create detailed policies and procedures so that everyone knows exactly what to expect when performing certain tasks. Additionally, you should ensure that any new hires understand the same things.
* Make use of automation tools.
Automation allows you to quickly identify potential risks without having to manually review thousands of files. As an added benefit, automated scanning helps prevent false positives from being reported.
* Use strong passwords.
Passwords aren’t just used to secure accounts; they’re also used to authenticate users during logins. Therefore, you should never reuse passwords. Instead, you should generate unique ones for each account. Also, you should avoid using weak password standards like “password” or “123456.” Instead, try creating complex passphrases made up of random words.
* Keep software updated.
Software updates help keep systems safe by fixing bugs and adding features. Unfortunately, many organizations fail to update their software because they think there isn’t time. But if you wait until all of your applications stop functioning, you’ll end up with outdated versions. So instead, you should schedule automatic updates at least once per week. You should also test patches thoroughly before deploying them.
* Implement multi-factor authentication.
Multi-factor authentication requires two forms of identification: something you know ( like a username) and something you possess. The idea behind this approach is to reduce the chances of someone stealing credentials. For example, you might require employees to enter both their usernames and tokens when logging in. If anyone tries to log in with only a username, he won’t get access unless he has his token. Similarly, if someone attempts to steal a user’s token, she won’t be able to gain access either.
* Restrict physical access.
Physical access controls are important because they provide additional layers of protection against unauthorized individuals. They include locks on doors, alarms, cameras, etc., but these measures alone may not be sufficient. To increase the effectiveness of physical access control, you should consider implementing biometric technology. Biometrics refers to technologies that rely on biological characteristics rather than traditional identifiers like names, addresses, social security numbers, and credit card information. Examples of biometric technologies include:
• Fingerprint scanners.
• Iris recognition devices.
• Facial recognition programs.
• Voice verification programs.
• Hand geometry analysis.
• Retinal scans.
• DNA testing.
• Even heartbeat detection.
These methods can significantly improve the accuracy of identity verification while reducing fraud rates. However, some people have expressed privacy concerns. In response, companies such as Google and Facebook offer services that allow customers to share data anonymously.
* Monitor network traffic.
Network monitoring provides insight into how attackers attempt to break into networks. It includes packet sniffing, port scanning, vulnerability assessment, intrusion prevention system alerts, and more. Network monitoring tools typically work by capturing packets sent over public networks. This means that any malicious activity will show up in logs. Some tools use deep packet inspection to analyze encrypted communications. Others simply monitor unencrypted connections. Regardless of which method you choose, IT administrators must review log files regularly.
* Use encryption.

Encryption scrambles sensitive information so that no one except authorized users can read or understand its contents. Encrypted messages cannot be deciphered without special knowledge. As a result, encrypting email attachments prevents hackers from reading confidential documents. Likewise, using strong passwords helps protect databases containing personal information. And finally, storing sensitive data offsite reduces exposure to cyber-attacks.
Reasons to consider CSPM over other cloud security solutions
CSPM has several benefits over traditional methods of assessing your cyber-security posture.
1. Works 24/7
Traditional approaches to managing security involve periodic audits and assessments. While this process works well for smaller organizations, larger enterprises need continuous visibility across all areas of operations. With CSPM, you’ll always know what risks exist within your organization. You don’t have to wait until an audit occurs before taking action. Instead, you can proactively identify potential threats and take steps to mitigate them immediately.
2. CSPM doesn’t require manual intervention
With traditional approaches to security, you must manually perform tasks such as reviewing reports and conducting penetration tests. By contrast, with CSPM, you only need to make changes when necessary. For example, if new vulnerabilities emerge during a scan, you won’t have to spend time updating software patches. Similarly, if malware attempts to infiltrate your systems, you won’t have time to respond. Automating processes allows you to focus on strategic initiatives instead of mundane details.
3. Uses artificial intelligence technology
Artificial Intelligence uses algorithms to learn patterns and predict future outcomes based on past experiences. AI enables computers to recognize objects, translate languages, play games, and much more. The same principles apply to cyber-security. When used correctly, AI can help detect anomalies and flag suspicious activities. For instance, if someone tries to gain unauthorized access to your servers, AI could alert you to the event. If you’re already aware of the threat, you can quickly address it. In addition, AI can also provide insights into network traffic and user behavior. These capabilities allow you to better manage your infrastructure and reduce downtime.
4. Provides real-time feedback
When you implement CSPM, you get immediate results. Unlike traditional approaches, where you may not see improvements for weeks or months after implementing fixes, CSPM gives instant updates. That way, you can react faster than ever before. This speed makes it easier to prevent attacks and minimize damage caused by breaches.
Conclusion
CSPM provides a comprehensive insight into how secure your environment really is. It’s easy to use and requires minimal effort. Because it automates many routine tasks, you can devote your attention to higher priority issues. Plus, because CSPM continuously monitors your system, you never miss out on important alerts. Finally, CSPM offers powerful analytics tools that enable you to analyze trends and spot emerging problems. All these features combine to give you complete control over your IT assets.